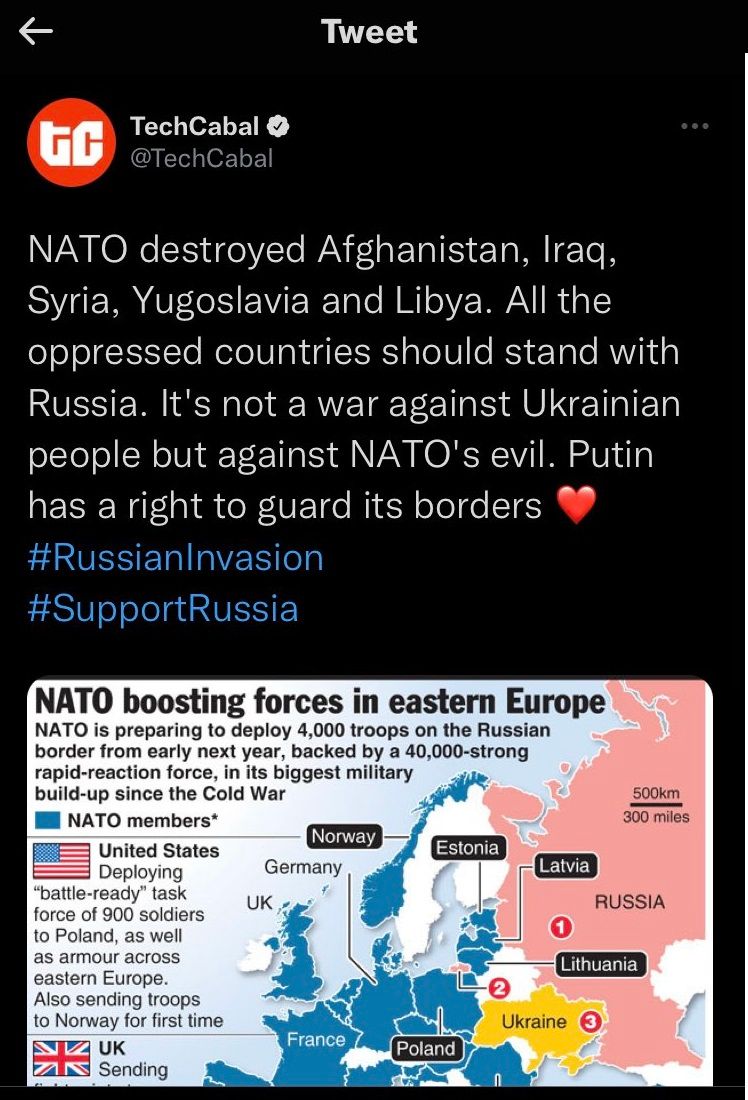
Sometime during the night of 27 February 2022, something peculiar appeared on Twitter. A tweet by Afrikan digital technology publication, TechCabal, appeared with a message in support of Russia's invasion of Ukraine.
Further searches of the hashtags that accompanied the tweet revealed more identical tweets from different Twitter accounts around the world.
"NATO destroyed Afghanistan, Iraq, Syria, Yugoslavia and Libya. All the oppressed countries should stand with Russia. It's not a war against Ukrainian people but against NATO's evil. Putin has a right to guard its borders ❤️ RussianInvasion SupportRussia," read the tweets.
Buffer customers hacked
It turned out that it was not only some Twitter, several other Linkedin and Facebook accounts are reported to have posted the same message. This was revealed through a statement by Buffer, a tool for managing social media accounts, in which the company also stated that the breach and/or hack happened at the customer level and not at Buffer.
According to Buffer, the breach of their customers' accounts likely happened because of re-used passwords.
"We’ve become aware that access was obtained to a number of Buffer accounts which have been used to spread support for Russia’s invasion of Ukraine. This is very concerning to us. So far there is no indication of a breach to Buffer. We will update this thread as we know more. This affected 1,552 accounts. Of those, 618 accounts posted unauthorized content. Our current understanding is that access was obtained through individual accounts, not through Buffer, likely through reused passwords, though we are not yet certain. Of the 618 Buffer accounts that posted unauthorized content, 766 posts were sent in total: - 505 (66%) to Twitter - 233 (30%) to Facebook - and 28 (4%) to LinkedIn Our team has taken steps to stop any further unauthorized posts from being sent. None of the 1,552 affected accounts had two factor authentication (2FA) enabled, further indicating that this was likely related to reused passwords. We are continuing to investigate. In the meantime, here’s how to turn on 2FA for your Buffer account," reads part of the statement by Buffer.
Two factor authentication disabled
It's important to note as Bufer also confirmed that none of the compromised accounts had two-factor authentication (2FA) enabled on Buffer. If 2FA was enabled it would have made it harder for the hackers to gain control of the accounts as they would need a second, different, method to authenticate themselves before being allowed to log in.
TechCabal promptly deleted the tweet.
"Our first priority has been investigating the unauthorized access into Buffer accounts while preventing future access and blocking suspicious traffic. Now, we are beginning the process of removing unauthorized posts and are aiming to successfully remove all unauthorized posts. Since our last update, our team has successfully removed unauthorized posts on Twitter and Facebook (96% of total posts). We’ve hit a snag with LinkedIn posts and are still working to remove those remaining 28 posts. Every impacted Buffer user whose account was affected has been contacted with recommended steps to take. If you were impacted or our team can help with anything please get in touch via hello@buffer.com."
— By Tefo Mohapi